Wireless networks are the lifeblood of modern offices, campuses, and homes, delivering fast connectivity without cables. This convenience carries significant security risk: attackers can listen to traffic over poorly protected channels, spoof trusted devices, or position rogue access points that lure legitimate users.
Misconfigurations, weak or reused credentials, and outdated encryption threaten data confidentiality and integrity at every layer of the network. As WiFi standards evolve, so do exploitation techniques that target flawed implementations, poor segmenting, and insecure onboarding. Understanding these risks is essential for defenders, auditors, and network engineers who must translate technical findings into practical protections that preserve uptime without sacrificing usability.
WiFi penetration testing helps organizations verify defenses before attackers do, identifying gaps in encryption, access control, and segmentation in a controlled, ethical manner. A rigorous assessment clarifies which configurations are most vulnerable, whether guest networks are isolated from critical resources, and how easily devices authenticate. By documenting risks and prioritizing remediation, pentesters support risk-based budgeting, policy updates, and user education. The goal is not to disrupt operations but to strengthen resilience against real threats such as credential theft, deauthentication attacks, and data leakage. Testing aligns with standards and best practices, producing actionable guidance for secure design.
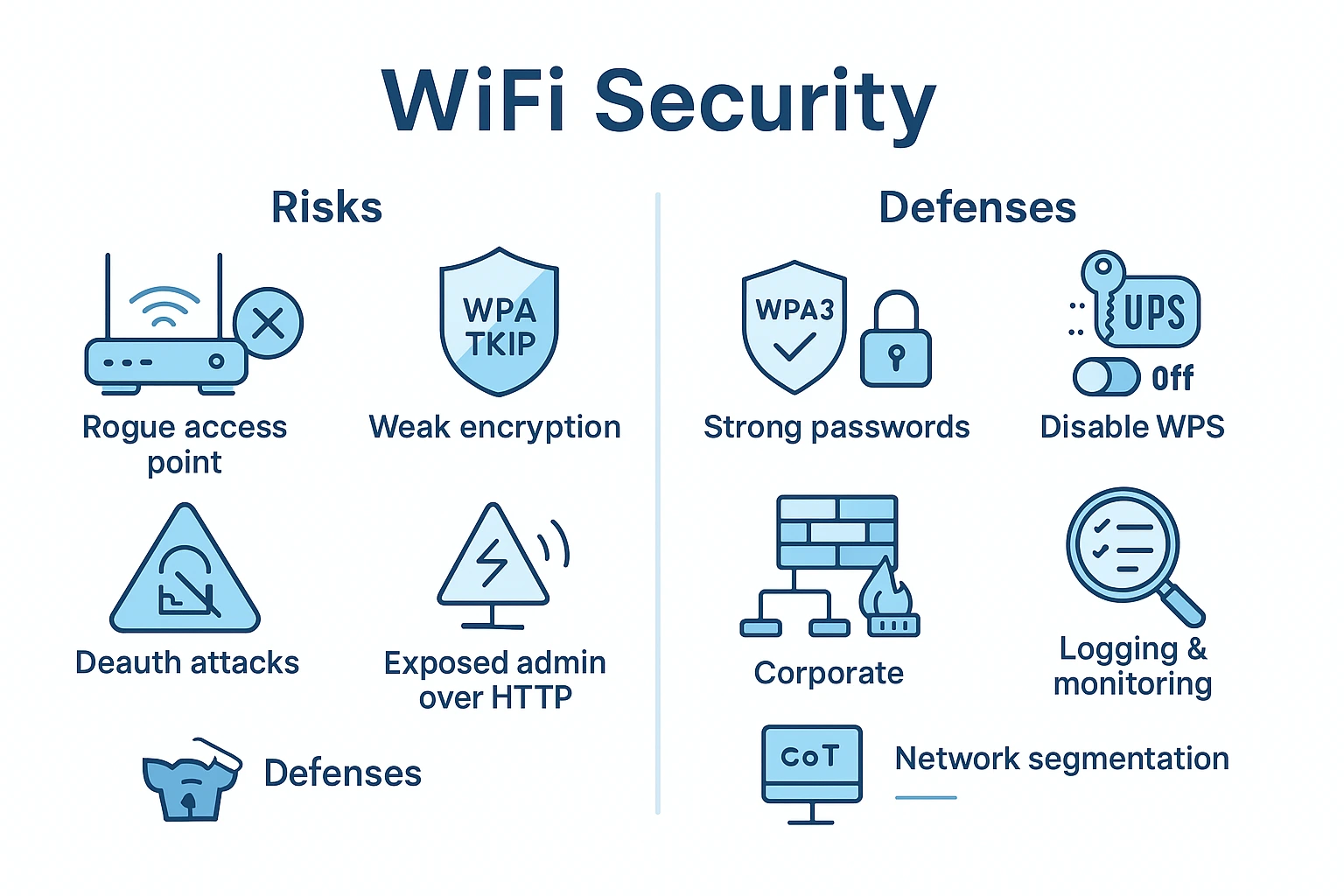
Common WiFi Security Flaws are revealed during WiFi penetration testing, demonstrating how attackers exploit weak configurations to access both office and home networks. In many environments, devices still rely on outdated encryption such as WEP or TKIP, or linger on legacy WPA modes, leaving data vulnerable to eavesdropping and credential theft. Even WPA2 with a strong passphrase can be undermined by misconfigured access points, weak administrator passwords, or unpatched firmware that enables known exploits. The result is a network where trust is ambiguous, and a prepared attacker can pivot from the wireless edge into adjacent systems, files, or cloud services.
Beyond encryption, configuration flaws significantly raise risk. Default administrator credentials are still present on many devices, and changes are rarely documented, allowing an intruder who is physically near the access point to log in quickly. Firmware without timely updates leaves routers exposed to exploits that bypass password protection and provide remote control. WiFi Protected Setup is frequently misused or left enabled, creating an easy avenue for brute force attacks and credential reuse. Insecure management interfaces, exposed via HTTP rather than HTTPS, enable spoofing, information leakage, and unauthorized changes even from trusted devices. Segmentation failures allow lateral movement into connected hosts.
Rogue access points and weak network isolation also appear as frequent security gaps during assessments. An evil twin or misconfigured guest network can lure clients into untrusted paths, where traffic is monitored or redirected. Open networks without captive portal controls, DNS protections, or secure onboarding invite credential sharing, expose users to credential harvesting and credential stuffing risks. Proper segmentation between guest, IoT, and corporate networks helps limit exposure, while centralized logging and regular audits reveal abnormal access patterns promptly. For defenders, recognizing these flaws through disciplined testing is the first step toward reducing risk, strengthening configurations, and maintaining wireless posture.
When performed by authorized professionals, WiFi penetration testing reveals security flaws hidden in wireless networks. If left unchecked, weak protections can lead to unauthorized access to data, disruption of services, and loss of trust. Pentesters must operate within legal and ethical boundaries; misused assessments or scope creep can itself create risk, including accidental exposure or service downtime. The testing process surfaces weaknesses such as insecure authentication, insufficient encryption, and insecure guest networks, and it emphasizes how attackers might move laterally from wireless access points into corporate systems.
In business environments, the impact can include data breaches, regulatory penalties, and operational downtime. Financial records, employee credentials, intellectual property, and customer information are at stake, with consequences ranging from fines under GDPR or PCI DSS to costly remediation and lawsuits. Reputational damage often follows a public breach, eroding customer trust and competitive advantage. The ripple effects touch supply chains, third-party vendors, and insurance coverage, complicating incident response. Even routine testing can uncover misconfigurations that create service interruptions if not managed properly, underscoring the need for careful scoping, change control, and communication with stakeholders to minimize impact. Effective remediation turns findings into resilient protections that bolster security, trust, and continuity across networks.
From a risk perspective, common findings include weak encryption, misconfigured access control, insecure guest networks, exposed management interfaces, and insufficient monitoring. No single flaw guarantees exploitation, but together they create pathways for credential theft, session hijacking, or network compromise. Real-world impacts also hinge on the asset's sensitivity, the presence of connected IoT devices, and the organization's exposure to external networks. Mitigation requires timely remediation, network segmentation, secure authentication, robust logging, and ongoing vulnerability management. By translating test results into prioritized risk remediation, organizations can reduce the likelihood and impact of wireless breaches while maintaining business continuity and customer confidence today.