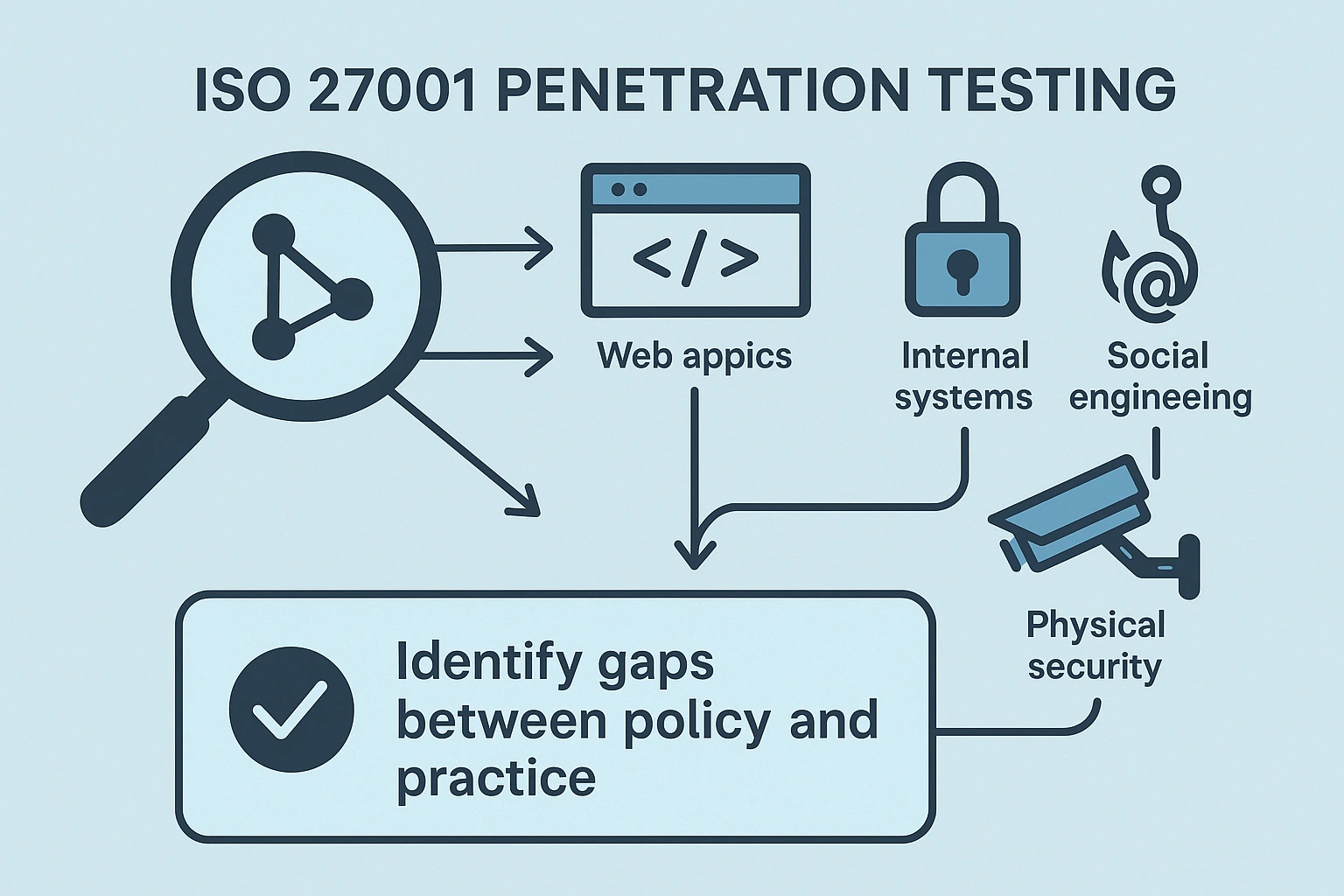
ISO 27001 penetration testing covers the practical assessment of an organization's information security controls as they exist in production. The process starts with scoping to align testing with the organization's ISMS boundaries, risk appetite, and legal constraints.
It then combines vulnerability discovery, configuration review, and simulated attacker techniques to reveal where policies diverge from practice. A quality test challenges both technical layers,—networks, servers, and applications—and human factors, including awareness and process maturity. The goal is not to break systems but to illuminate exploitable weaknesses before real adversaries do.
Deliverables typically include a detailed findings report, evidence of testing, and a risk-based remediation roadmap that aligns with ISO 27001 controls. Testing scopes commonly cover network perimeters, web applications, APIs, and internal systems, as well as secure configurations, access control, authentication flows, and data handling practices. In many programs, social engineering simulations, such as phishing, are included to evaluate human resilience, while physical security tests assess entry controls and environmental risk. The assessment also considers change management and monitoring gaps, ensuring that new risks are not introduced during updates.
A rigorous ISO 27001 penetration testing methodology begins with scoping, asset discovery, and a risk assessment. The tester works with stakeholders to define objectives, boundaries, and success criteria, ensuring alignment with the organization's information security policy and the ISO 27001 controls. A risk-based plan guides testing priorities, focusing on critical assets, data flows, and exposed interfaces.
Execution combines controlled information gathering, vulnerability assessment, and targeted testing to validate security controls without disrupting operations. The testers use a risk-based matrix that maps findings to asset criticality, impact, and relevant ISO 27001 controls, enabling consistent severity ratings. Where permissible, safe testing steps simulate attacker techniques to confirm potential exploit paths while thorough logging and evidence collection ensure reproducibility.
Reporting closes the loop by delivering an ISO 27001-aligned report that translates technical findings into actionable controls and risk outcomes. The executive summary highlights business impact, while the technical body maps each finding to controls, owners, and remediation steps. The report includes evidence, timelines, and a prioritization of quick wins and longer-term mitigations, plus recommendations for compensating controls where gaps exist. A retesting plan and a continuous improvement roadmap ensure ongoing alignment with the ISMS and assist during ISO 27001 audits.