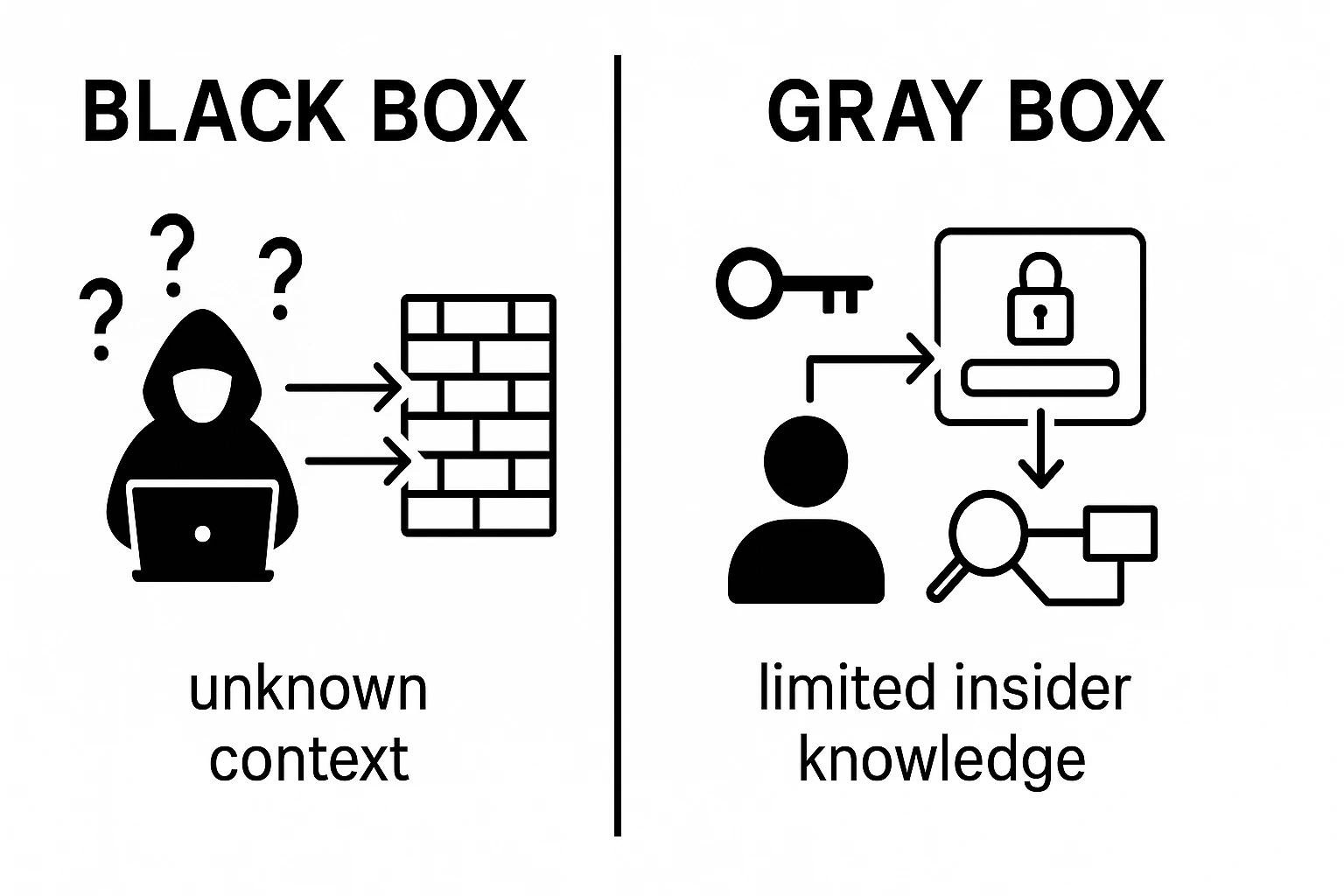
Black box penetration testing simulates an external attacker who has little to no knowledge about the target's internal structures. In this approach, testers begin with surface information and work outward, reproducing how a real adversary would probe web apps, networks, and infrastructure from the internet edge. The objective is to uncover misconfigurations, exposed services, insecure authorizations, and logic flaws that are visible without internal credentials or detailed maps of the system.
The process typically includes goal definition, scoping, reconnaissance, threat modeling, vulnerability assessment, exploitation, and post exploitation analysis, all while documenting evidence and risk impact. Because access to source code, architecture diagrams, or internal credentials is intentionally restricted, outcomes reflect realistic external risk and help prioritize remediation based on external exposure.
However, black box testing can be less comprehensive in depth compared with gray box or white box testing, particularly for complex logic errors or privileged pathways that require insider knowledge. It also depends heavily on tester skill and time, since the lack of internal context can slow discovery. In the broader discussion of Black Box vs Gray Box Penetration Testing, the main difference lies in the amount of information available at the outset. Gray box offers partial insight, too.
Gray box testing is a middle-ground approach between testing with no information about the system (black box) and testing with full inside knowledge (white box). Testers start with a small amount of inside information—such as a few user login details, a basic map of the main systems, or a rough view of how the network is arranged—and then try to break in the way a real attacker would. This mix helps assess both what an outside attacker could discover and what someone who already has some access could do. It looks at login procedures, security controls, who can access which parts, and how someone could gain higher permissions. By combining partial inside information with outside exploration, gray box testing can uncover setup mistakes and logic flaws that pure external testing might miss, while avoiding the heavy effort of a full, all-access security review.
In practice, gray box engagements are risk-based and scope-driven. Clients provide limited access, such as test accounts, credentials, or sample network maps, while leaving sensitive code paths and vendor systems out of scope. The tester's workflow emphasizes critical assets, user authentication flows, role-based access, and trust boundaries rather than exhaustive surface coverage. Findings typically include actionable remediation for misconfigurations, weak passwords, session management gaps, and segmentation faults, with a prioritized report that maps risks to business impact. When used appropriately, gray box testing balances depth, speed, and cost to deliver meaningful security insights. It complements regulatory needs well.